TL;DR: Weak passwords are the easiest point of entry for hackers. Here’s how to protect yourself.
- Password reuse
- Predictable changes
- Destructive behaviors
- Overcoming the hackers
- Potential negatives
- Choosing a password manager
- Securing your future
Did you know that 80% of data breaches are caused by compromised, weak, and reused passwords?
With cybercrimes on the rise, keeping our passwords safe and secure is more critical than ever.
How many logins do you have?
Personal email, work email, all your different social media accounts, all the programs you use at work, shopping sites, entertainment sites, etc. They add up quickly and keeping all of them up with password best practices can be a lot of work
The average internet user has more than 90 different logins. Best practice password policies suggest having a unique, complex login for each of those different logins.
Do you have 90 phone numbers memorized? Not likely and even less likely you have more than 10 unique and random passwords memorized for some of those logins.
Most of us have little tricks to make life easier for us. We might reuse a password for several different services or use a simple system for updating passwords when necessary. Unfortunately, these bad habits often expose us and increase the likelihood we’ll fall victim to a hack.
Thankfully there is a simple solution that not only helps us keep our passwords strong and secure, but makes our lives easier as well. Before we dive into the solution, let’s be sure we understand the problems the solution is fixing for us.

Password reuse
We’ve all done it. In fact, a survey found that more than 50% of us reuse the same password all the time. We create one super clever, but easy for us to remember, password. We then use it for every single login.
So you don’t feel judged, I’ll share my embarrassing password from the early days of the internet. Don’t be too hard on me, we didn’t know then what we know now. At the time, I thought it was a pretty good one. After all, I was using uppercase and lowercase letters and a number!
Yummy1
Don’t worry, I’m not using this password for any services or websites anymore. I did, however, use this one password on every site for YEARS. I felt pretty secure compared to my friends using things like “oreosaregood” or, yes someone I know actually used this – “password123.”
Checking my reused password today:
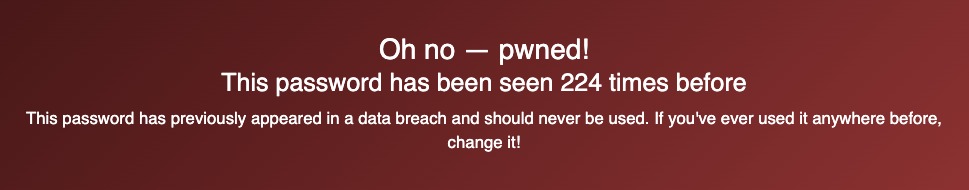
That’s not good! Still better than password123:
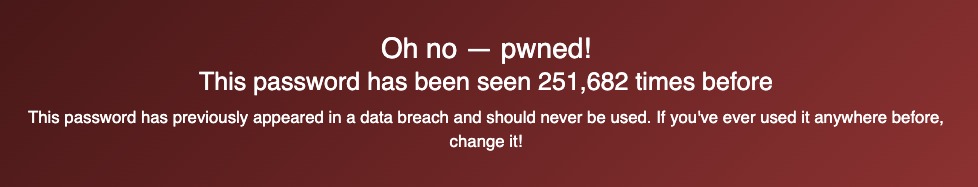
Yikes!
New businesses and websites get breached every day. If your information was part of a breach and you use the same email address (or username) and the same password for several websites and services, now hackers will have the necessary information to access those accounts as well.
You change it… predictably
Reused passwords aren’t the only way hackers gain access to your accounts. When you forget a password or are forced to reset it, do you come up with a completely new password? Or, are you like most people and set your new password to something very similar to your current password? A majority of online users will often make a simple update like changing or capitalizing one character. You might update the year’s date or increase a previous value by one.
For example, let’s pretend password$20 is a good password (it’s not). You’ve used this for years, and then suddenly, one of the services you use requires you to update your password to fit their new rules. You need to have a capital letter, and you need it to be longer than 12 characters. Most people will capitalize the first letter and extend/update the year. So, the new password becomes Password$2021. Technically it’s longer and harder to crack, so it’s more secure, right?
Not quite.

Why are these two behaviors so destructive?
Hackers know and have developed automated systems that test for these behaviors.
They begin by checking against a giant master list that contains every dictionary word and any password that’s been part of a data breach. One of these master documents has over 8 billion commonly used words and passwords (this is why it’s so important you don’t reuse passwords).
Then they use automated software to check common variations around passwords. They’ll check if the first letter has been capitalized or if the end number was raised by one. If you’ve been part of a previous breach and they have your original password, they will test common variations on that old password.
Don’t worry. It’s easy to break this system
It’s not all doom and gloom for you though. Thankfully, hackers are just as predictable. Generally, they pursue the path of least resistance.
Complex passwords take years to crack from scratch. With limited time and resources, hackers use automated software to check for common patterns among predictable options – reused passwords or those that use slight variations.
Predictable patterns are easy to hack. Randomness cannot be predicted.
If you have 90 different sites and follow guidelines suggesting you change your passwords every three months…that’s 360 random passwords a year! Unfortunately, the human brain isn’t built to be random.
That’s why password managers are so great.
What a password manager does for you:
- Randomize your passwords
- Store your passwords
- Notify you if your password has been compromised
Would you be able to come up with and remember – YxvE#WWLtzCE_~wU.6w#B@tE,?
Unless your brain is built like a computer, probably not. Most password managers suggest completely random passwords based on the criteria you chose. They can be long, complex, and, most importantly, super random. Something we can’t do on our own.
Once you have your complex and random password, your password manager will store it for you in a secure vault (we’ll talk about this more in a bit). Then, because they are storing your passwords for you (and you’re no longer writing them down on a post-it note), you can use their software and browser add ons to make it really easy to fill in your login details when you need them.
Password managers can also notify you if your password has been part of a breach, if you’re reusing a password with another website or service or if the site you’re logging into uses outdated technologies like HTTP (vs HTTPS). 1Password partners with Have I Been Pwned to check if your information has been part of a recent breach. As an added bonus, some password managers can give you helpful reminders about some of the information you choose to store. For example, if you add your passport details inside the 1Password app, it will remind you when it’s about to expire.

Are there any negatives?
The most common argument is that password managers become a single point of failure and are high risk. For example, if a hacker breaks into the password manager’s servers, they will gain access to all your accounts. All your security eggs are in one basket, so to speak.
Yes, you have all your passwords in a centralized place, but stealing this information is much easier said than done. Besides, if you’re reusing the same passwords, this is already the case anyways.
Are they really that secure?
The short answer, yes.
Most (if not all) of the major password managers use AES 256-bit encryption to encrypt and store your saved data. We’re not going to give you an entire lecture on cryptography, but trust us, the math behind this encryption method is staggering. Currently, this is the highest level being used by the US government. The number of possible combinations one would have to guess with this system is astronomical. There are more possible combinations with this encryption than there are atoms in the observable universe.
Or think of it this way, assume there are 7 billion people on earth, and every person has 10 computers. If the entire population combined all their computing power, then they would be able to crack an AES 256-bit encryption key—in 77,000,000,000,000,000,000,000,000 years!
Further, they combine the encryption methodology with a complex encryption algorithm to generate a secret key only known to you. That way, even if hackers do manage to get into the password manager vault, all they’d get away with is a lot of unusable encrypted data that would be gibberish. In order for the hacker to make that data usable and view your passwords, they would also need to find a way to steal your secret key from you.
Which password manager is right for me?
There are a few options that have been around for several years to choose from. In the end, your choice comes down to budget and features. Here are a few options you can review and decide which works best for you:
1Password (what we use and our our recommendation), Bitwarden, KeePass
Most offer some level of free service or trial period, so you can play around with them and get a feel for which one works best for you. Be sure to install their apps and browser add ons for the ultimate ease of use and full experience from the service provider of your choice.

Securing your future
Cybercrime is expected to grow into a $10 trillion industry by 2025. Thankfully, security solutions and products are increasing as well. A lot of internet and web security involves complex changes and patches that must be applied at the administrative level.
Luckily password security can be handled simply by using a solid password manager. By offloading complex password generation, encryption, and storage to an outside service, you stop practicing the predictable patterns and behavior hackers love, add a much needed barrier of protection around your passwords, while also freeing up a little more of your precious time to focus on other things.
While cybercrime is scary and these threats do exist, small changes to your behavior and processes go a long way to securing your online presence. Often, we use services and sites that add layers of extra security for us and it never hurts to have an extra set of eyes on the important things to make sure everything is as protected as it can be.
Want to improve your WordPress security? Reach out to us now for more information!


